Meltdown-Spectre/Meltdownについて、ここに記述してください。
https://meltdownattack.com/meltdown.pdf
1. Address Space
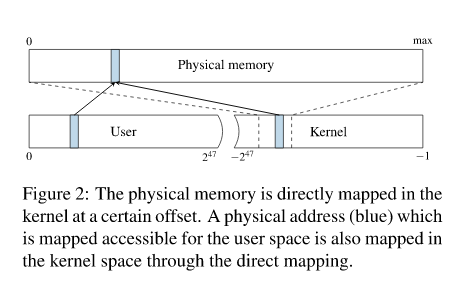
the entire physical memory is typically mapped in the kernel.
On Linux and OS X, this is done via a direct-physical map, i.e., the entire physi-cal memory is directly mapped to a pre-defined virtual address (cf. Figure 2).
Instead of a direct-physical map, Windows maintains a multiple so-calledpaged pools, non-paged pools, and the system cache. These pools are virtual memory regions in the kernel address space mapping physical pages to virtual addresses which are either required to remain in the memory (non-paged pool) or can be removed from the memory because a copy is already stored on the disk (paged pool).
The system cache further contains mappings of all file-backed pages. Combined, these memory pools will typically map a large fraction of the physical memory into the kernel address space of every process.
2. cache attacks
Flush+Reload attacks work on a single cache line granularity. These attacks exploit the shared, inclusive last-level cache. An attacker frequently flushes a targeted memory location using the clflush instruction. By measuring the time it takes to reload the data, the attacker determines whether data was loaded into the cache by another process in the meantime. The Flush+Reload attack has been used for attacks on various computations, e.g., cryptographic algorithms [35, 16, 1], web server function calls [37], user input [11, 23, 31], and kernel addressing information [9].
